Sophos XG Firewall Custom Response Integration
This article shows how to leverage the Lumu Defender API and Sophos XG API to mitigate security risks.
Requirements
-
Sophos XG Firewall
-
A Sophos XG Firewall with SFOS 19.0.0 GA-Build317 with the Xstream Protection bundle (Network Protection and Web Protection) is required.
-
Lumu Defender API key
- To retrieve an API token, please refer to the
Defender API
document.
-
Script host
- Host with Python 3.10+ with network visibility over Lumu Defender endpoints and Sophos XG Firewall.
-
Script package
- Contact the
Lumu support team
to request the package we created to deploy the required files.
Set up the Sophos XG API
Add an administrator role for Lumu integration
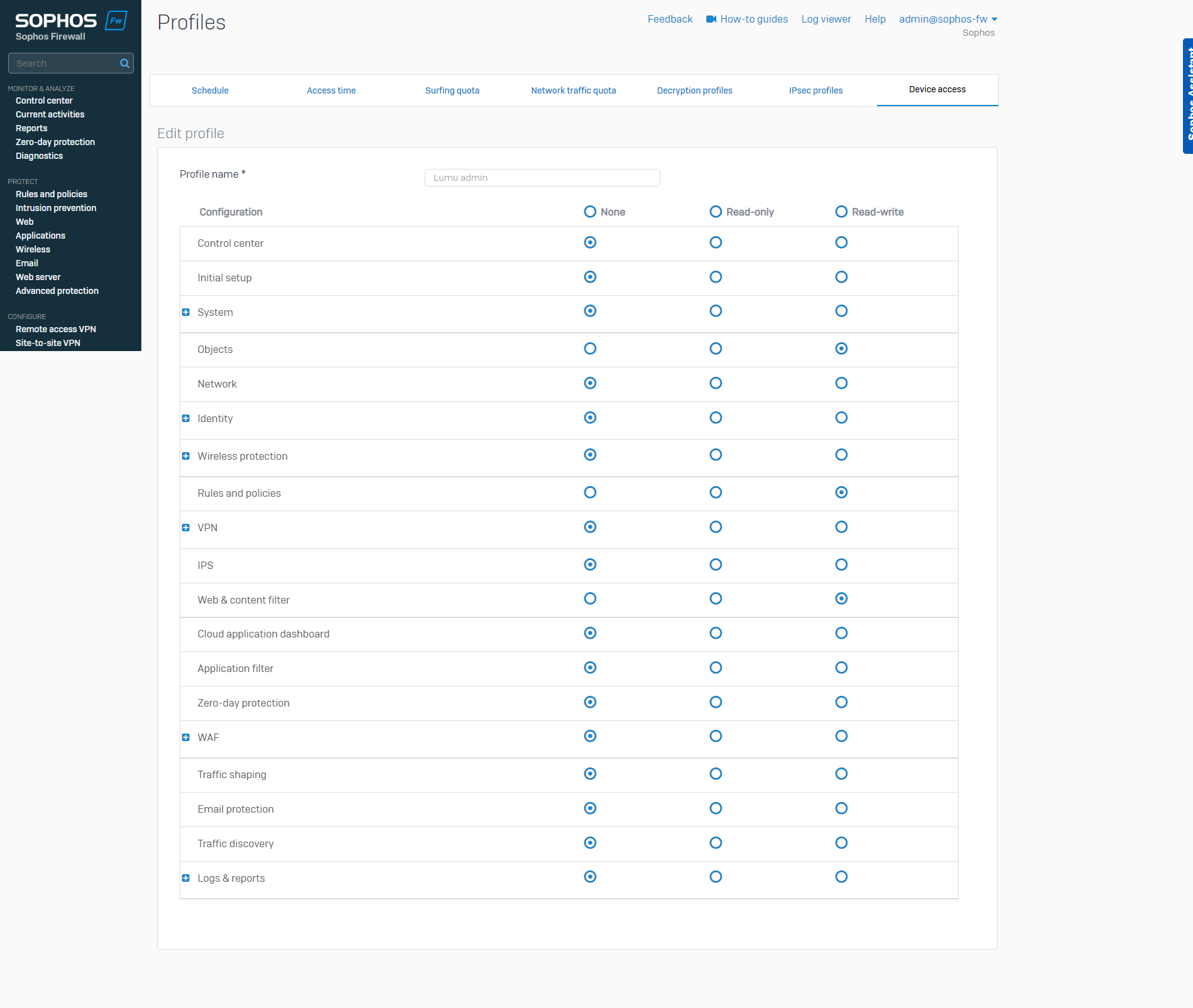
1. Using the Sophos XG Web console, go to the Profiles menu under the SYSTEM section.
2. Click on the Device access tab, and then on the Add button.
3. Give a name to the profile and enable the Read-write permissions for the Objects , Rules, and policies , and Web & content filter configurations .
Add a new administrator user
1. Go to the Authentication menu under the CONFIGURE section.
2. On the Users tab, click the Add button. Fill in the required information.
3. In the
User type
select
Administrator
, and in the
Profile
field list, select the profile created in the previous step.
Enable the API
1. To enable the API in your Sophos XG Firewall, go to the Backup & Firmware menu under the SYSTEM section.
2. Go to the API tab, then, under the API configuration section, toggle the API configuration button, and fill in the Allowed IP addresses .
3. Finally, click the
Apply
button to save your changes.
Deploy the script
First, contact the Lumu support team to request the deployment package.
Scripts location
Unpack the deployment package provided by Lumu in your preferred path/folder. Keep in mind this location, as it will be required for further configurations. From now on, we will refer to this folder as <sophosxg_lumu_root> .
In the package, you will find the script required to run the integration. To use the script, you must locate yourself on the path selected for deployment ( <sophosxg_lumu_root> ). Specific directions are included in the next sections.
Install requirements
The file requirements.txt contains the list of requirements for this integration. After deploying the package locally, run the following command from the deployment folder:
Script details
To use the script, you must locate yourself on the path selected for deployment ( <sophosxg_lumu_root> ). Use the following command to show all options available for the package:
Usage: sophosxg_lumu.py [options]
|
Options |
Description |
|---|---|
| -h, --help | show this help message and exit |
| --config CONFIG | Load options from config file |
| --company-key COMPANY_KEY--company_key COMPANY_KEY | Lumu Company Key (Defender API). |
| --proxy-host PROXY_HOST--proxy_host PROXY_HOST | Proxy host (if required) |
| --proxy-port PROXY_PORT--proxy_port PROXY_PORT | Proxy port (if required) |
| --proxy-user PROXY_USER--proxy_user PROXY_USER | Proxy user (if required) |
| --proxy-password PROXY_PASSWORD--proxy_password PROXY_PASSWORD | Proxy password (if required) |
| --logging {screen,file} | Logging option (default screen). |
| --verbose, -v | Verbosity level. |
| --adversary-types {C2C,Malware,DGA,Mining,Spam,Phishing}--adversary_types {C2C,Malware,DGA,Mining,Spam,Phishing} | Lumu adversary types to be filtered. |
| --days DAYS | The number of days backward from now to query Lumu incidents (default 30). |
| --test, -t | Runs a test with one incident only. |
| --old-clean--old_clean | Cleans all rules and objects created by the Lumu integration. |
| --clean | Cleans all rules and objects created by the Lumu integration. |
| --host HOST | Sophos XG firewall hostname or IP address. |
| --username USERNAME | Sophos XG firewall username. |
| --password PASSWORD | Sophos XG firewall password. |
| --ioc-types {ip,domain,url}--ioc_types {ip,domain,url} | IOC types to be collected and processed by the integration. If 'domain' and 'url' are selected, 'url' will be processed (default 'ip', 'url'). |
| --base-name BASE_NAME--base_name BASE_NAME | Sophos XG base object name (default Lumu). |
| --web-policy WEB_POLICY--web_policy WEB_POLICY | Web policy to update if 'url' IOC type is selected. |

Usage Examples
Task: query and add indicators (IPs and URLs) related to Lumu incidents
Use the following command to fetch and push to Sophos XG firewall IPs and URLs IOCs related to incidents found in your organization by Lumu in the last 30 days:
The integration creates a new IP host group Lumu IPs and related IP hosts with the prefix Lumu_ . For web filtering, it creates new Web filtering categories named with the Lumu Web prefix. Each Web category contains the URLs. Also, the integration adds a new rule at the beginning of the Web policy in block mode.

Task: query and add indicators (IPs, domains, URLs) related to Lumu incidents
This example will push domains under the FQDN host group in Sophos named Lumu Hosts .

Task: query and add indicators related to Lumu incidents with contacts in the last X days
Use the following command to fetch and push to your Sophos XG Firewall IOCs related to incidents found in your organization by Lumu with contacts in the last X days.

Task: query and add indicators related to Lumu incidents of specific types
By default, the script queries open and closed incidents of all adversary types (Phishing, Malware, Spam, others). If you need to collect specific types of incidents, you can use the argument --adversary-types ADVERSARY_TYPE. If you need to get two or more adversary types, you only need to append a new instance of the argument.
In this example, the adversary types queried are Phishing and Malware .
Task: clean all changes made by Lumu integration
If you need to delete all objects created by this integration in your Sophos XG Firewall, use the --clean flag with the authentication arguments.

Task: save log output to file
By default, you will see the execution log on the screen console. Use the argument --logging file to store a record of all tasks run in the lumu.log file in the script root path.
This file is useful for scheduled tasks or processes running in the background. When you open this file, you will see the following. The information displayed aids in checking the execution progress.
Task: use a configuration file to run the integration
You can run the integration using a configuration file where you can save the required arguments in form of <argument_name>=<value> , one argument per line. In the integration root path, save a file named .config with your configuration. Following, you have a sample of the format of the file
- ## Sample .config file
# Sophos XG
host=<sophos_ip_or_host>
username=<sophos_username>
password=<sophos_password>
web_policy=<sophos_web_policy>
# Lumu
company_key=<lumu_company_key>
# Misc
# Optional arguments
ioc-types=ip
ioc-types=domain
ioc-types=url
# Optional arguments (default all adversary types)
#adversary-types=C2C
#adversary-types=Mining
# Optional (default days: 30)
days=30
# Output trace to file. Relevant for cron job or scheduled task
logging=[screen|file]

Other tasks
According to your needs, you can combine the examples shown.
Expected results
You will see new objects in your Sophos XG Firewall:
Lumu IPs
in host groups, IP objects with the prefix
Lumu_
in IP hosts, and a Web category named
Lumu Web
.
Lumu IPs host group
Set up Sophos XG policies
After the custom objects have been created and maintained by the integration, you need to use it inside Firewall policies. Here, some examples of how to use these inside your Firewall policies:
Further considerations
To run the script on a timely basis, consider implementing a Scheduled task in Windows or a Cron task in Unix-based systems. If you are pushing hashes, the integration could take longer to run. We recommend that the scheduled job runs every 30 minutes.
Following, you have an example of how this Cron job should look using the recommended time.
It’s recommended to add the --logging file argument to any scheduled task. It will record all the output in the log file for further reference. If you have created a configuration file, your crontab entry doesn’t need any arguments. It should looks as follows:
If you need to work with another scheduling time, you can use the crontab guru.
To avoid race conditions, you can run only one instance. If you have one running, the second one will be canceled immediately.
Troubleshooting and known issues
To identify failures in the script execution, use the -v flag. The script execution log will show more detailed information.
If you receive the following error.
There could be another instance running. To check this, open the pid.pid file in the integration’s folder. This file stores the process id if it’s running. Search for this process in your system. The following pictures show the process in Windows and Linux.
Check integration process - Linux
If the previous validation indicates that another instance is running, please, check its progress using the integration’s log
lumu.log
.
Related Articles
Sophos UTM SG Custom Response Integration
This article shows how to leverage the Lumu Defender API and Sophos UTM SG API to mitigate security risks. Requirements Sophos UTM SG subscription You need a Sophos UTM SG with Firewall and Web filter capabilities. Lumu Defender API key To retrieve ...Bitdefender Custom Response Integration
Bitdefender Custom Response Integration This article shows how to leverage the Lumu Defender API and Bitdefender API to mitigate security risks. Requirements GravityZone Business Security Enterprise, cloud version, ...WatchGuard Firebox Firewall Custom Response Integration
Due to the lack of API support of WatchGuard Firebox Firewalls (without Firebox Cloud), this example emulates the access and configuration steps a regular admin user would run to feed URLs into the Blocked Sites option. This integration script is ...Sophos Antivirus Custom Response Integration
Before going through this article, check our Out-of-the-box App Integrations category . This is the recommended way to integrate the components of your cybersecurity stack with Lumu. If the product you are looking to integrate is there, it is advised ...SentinelOne Custom Response Integration
This article shows how to leverage the Lumu Defender API and SentinelOne REST API to mitigate security risks. Response setup leveraging Lumu detections with SentinelOne Requirements SentinelOne Singularity Control subscription A SentinelOne ...