Sophos Endpoint Protection Out-of-the-Box Response Integration

Requirements
- Sophos Central
- Sophos Central Account Access.
- API Token. You can obtain it in the API Token Management console.
- Lumu License
- An active Lumu Defender subscription
Configure Sophos Central
1. Log in on the Sophos Central UI
2. Click on the Global Settings option.
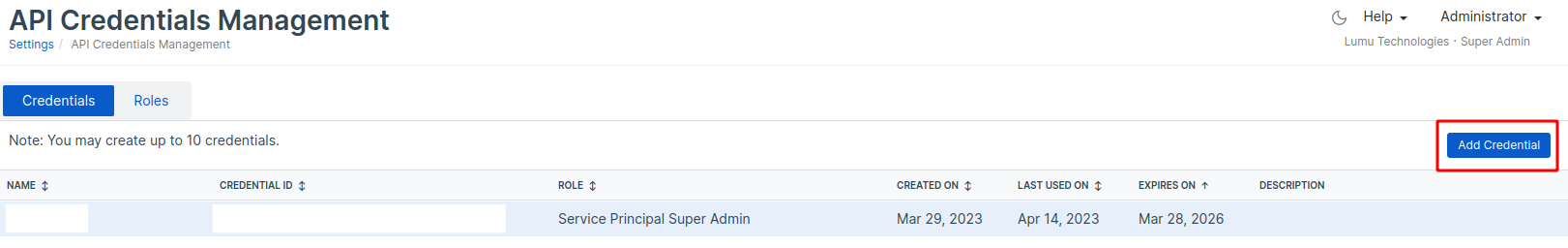
3. Click on the API Management credentials option to create the credentials for API use.
4. Click on Add Credential .
 5. Create a personal Credential with the Service Principal Super Admin Role.
5. Create a personal Credential with the Service Principal Super Admin Role.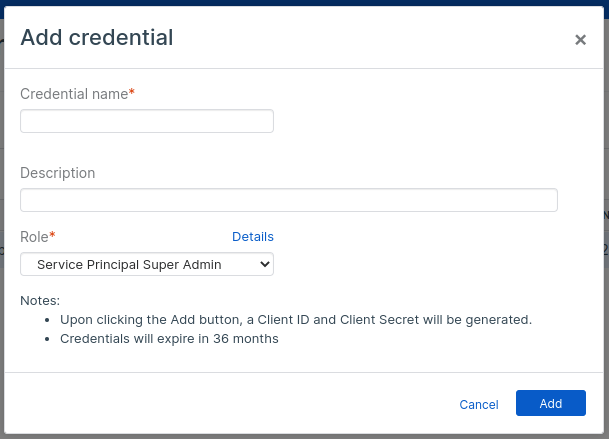
6. You will see something like the following. Save your Client Secret in a secure place.
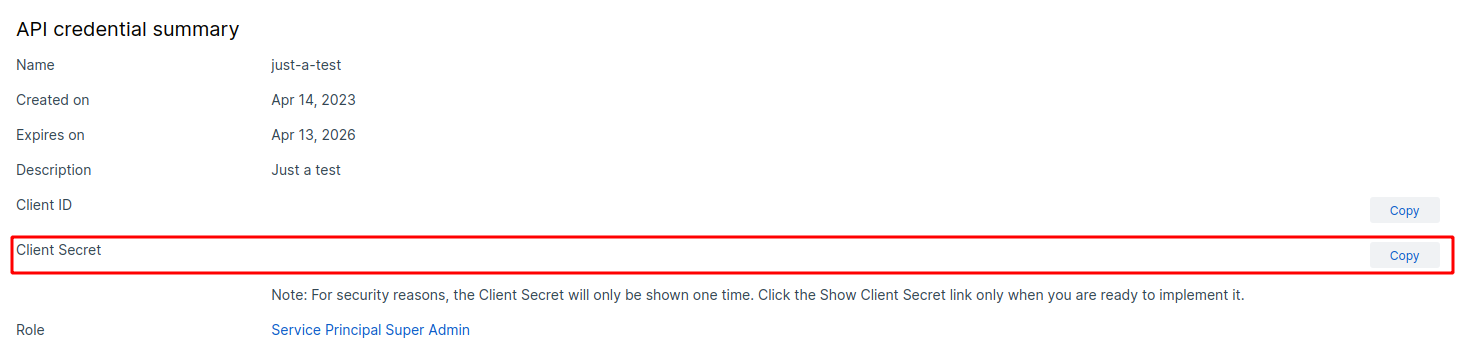
 Lumu encrypts this information both in transit and at rest to ensure token confidentiality is maintained.
Lumu encrypts this information both in transit and at rest to ensure token confidentiality is maintained.
Add Integration
1. Log in to your Lumu account through the Lumu Portal and navigate to the available apps screen.
2. Locate the Sophos Endpoint Protection integration in the available apps area, then click Add to view details.
3. Familiarize yourself with the integration details available in the app description and click the button below to activate the integration.
 Do not modify the “Lumu IOCs” tag name under Website Management or the Blocked Item list records.
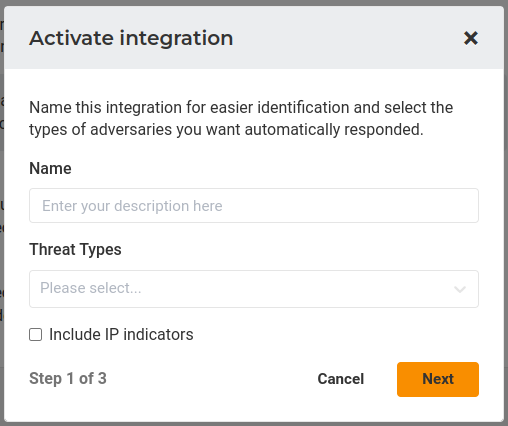
Do not modify the “Lumu IOCs” tag name under Website Management or the Blocked Item list records.4. Add a Name, and select the Threat Types that you want to push to your Sophos Control cloud. If you want to include IP indicators, you should select the option “ Include IP indicators “. Finally, click on the Next button.
 The integration adds URLs, domains, and file hashes by default.5. Fill in the Client ID, and the Client Secret for that account. Finally, click on the Next button.
The integration adds URLs, domains, and file hashes by default.5. Fill in the Client ID, and the Client Secret for that account. Finally, click on the Next button.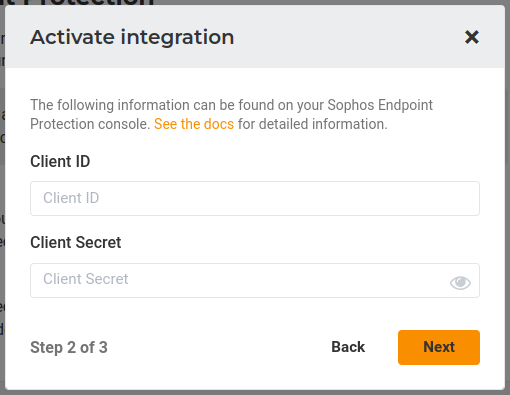 Lumu will validate if the credentials provided are correct.
Lumu will validate if the credentials provided are correct.
Configuration for Single Tenant accounts
6a. Here you will see your
Tenant ID
and the corresponding
base URL
of your Tenant.
Configuration for Partner or Organization accounts
6b. You will need to select the
Tenant Name
that you want to work with.

7. The integration is now created and active. Now, the Lumu Portal will display the details of the created integration:
Configure Threat Blocking
The final step to set up this automated response integration is to configure Sophos to block the threats detected by Lumu. To do so, follow these steps in your Sophos Central Web console to configure your Sophos policies to block navigation to the Lumu tag.
- Click on the Endpoint Protection link in the left navigation bar.
- Under the CONFIGURE section in the Endpoint Protection navigation bar, click on Policies .
- Select and modify your Web Control policies to block traffic to the Lumu tag. Click on the policy, and go to the Settings tab.
-
Under the
Settings
window, enable the
Control sites tagged in Website Management
. Add a new tag, select the
Lumu
tag, and set the action to
Block
. Save the policy.
 Remember to enable the
SSL/TLS decryption of HTTPS websites
feature under the
Threat Protection Policy
Remember to enable the
SSL/TLS decryption of HTTPS websites
feature under the
Threat Protection PolicyGet an AI Summary
Related Articles
Lumu Out-of-the-box Integrations
For getting started with Lumu integrations with third-party solutions, consult our Integrations guide. Lumu's Out-of-the-box (OOTB) integrations are a seamless and convenient way to integrate Lumu with other solutions in your cyberdefense stack to ...Sophos Enhanced Out-of-the-box Response Integration
Lumu can be integrated with other cybersecurity solutions to streamline response processes, including Sophos Firewall, and among the integration possibilities between Lumu and Sophos Firewall, we have the Enhanced OOTB Integration. The Enhanced OOTB ...Sophos Firewall Out-of-the-Box Response Integration Setup Primer
Lumu can be integrated with other cybersecurity solutions to streamline response processes, including Sophos Firewall. The Sophos Firewall Out-of-the-Box integration provides two distinct modes to support the flexibility and capabilities of Sophos ...Cylance Endpoint Security Out-of-the-Box Response Integration
This article describes the required procedure to integrate Cylance Endpoint Security with Lumu for automated response procedures. This is one of our featured Out-of-the-Box Response Integrations. Requirements Below you will find the technical ...Harmony Endpoint Out-of-the-Box Response Integration
This article describes the required procedure to integrate Harmony Endpoint with Lumu for automated response procedures. This is one of our featured Out-of-the-Box Response Integrations. Requirements An active Harmony Endpoint Basic or above ...