Trend Micro Web Security Custom Response Integration


Requirements
- Trend Micro Web Security Admin user.
- Two-factor authentication must be disabled.
- An administration user with email authentication is required
- Lumu Defender API key.
- To retrieve an API token, please refer to the Defender API document.
- Script host
- Host with Python 3.10+ with Internet visibility over Lumu Defender endpoints and Trend Micro Web Security URLs.
- Script package.
- Contact the Lumu support team to request the script deployment package.
Set up Trend Micro Web Security
Define the Customized URL category name
Define the name you want to use for the Lumu Customized URL category. Make sure this name is unique and it is not used in another category.

Prepare Python on your environment
As a recommended practice, we encourage you to create a Virtual environment for each integration to avoid conflicts between them and your operating system tools. Make sure you follow the steps in our Preparing Environment for Custom Integrations article.
Deploy the script
Script location
Unpack the deployed package provided by Lumu in your preferred path/folder. Keep in mind this location, as it will be required for further configurations. From now on, we will refer to this folder as <tmws_lumu_root> .
Install requirements
The file requirements.txt contains the list of dependencies for this data collector. After deploying the package locally, run the following command from the deployment folder:
Script details
To run the script, you must locate yourself on the path selected for deployment ( <tmws_lumu_root> ). Use the following command to show all options available for the package:
Usage: lumu-tmws.py [options]
| Options | Description |
| -h, --help | show this help message and exit |
| --config CONFIG | Load options from config file |
| --company-key COMPANY_KEY--company_key COMPANY_KEY | Lumu Company Key (Defender API). |
| --proxy-host PROXY_HOST--proxy_host PROXY_HOST | Proxy host (if required) |
| --proxy-port PROXY_PORT--proxy_port PROXY_PORT | Proxy port (if required) |
| --proxy-user PROXY_USER--proxy_user PROXY_USER | Proxy user (if required) |
| --proxy-password PROXY_PASSWORD--proxy_password PROXY_PASSWORD | Proxy password (if required) |
| --logging {screen,file} | Logging option (default screen). |
| --verbose, -v | Verbosity level. |
| --user USERNAME--username USERNAME | Trend Micro Web Security user. |
| --password PASSWORD | Trend Micro Web Security password. |
| --adversary-types {C2C,Malware,DGA,Mining,Spam,Phishing,Network Scan}--adversary_types {C2C,Malware,DGA,Mining,Spam,Phishing,Network Scan} | Lumu adversary types to be filtered. |
| --days DAYS | The number of days backward from now to query Lumu incidents (default 30). |
| --custom-category CUSTOM_CATEGORY, --custom_category CUSTOM_CATEGORY | Custom category to be populated. If it doesn't exist, the integration tries to create it (default Lumu). |
| --clean | Cleans all rules and objects created by the Lumu integration. |
Usage examples
Task: query IOCs (URLs) related to Lumu incidents for the last 30 days
Use the following command to fetch and push all adversaries detected by Lumu in the last 30 days to Trend Micro Web Security Custom URL Category.

Task: query IOCs (URLs) related to Lumu incidents for the last 30 days and push them into a Custom category
Use the following command to fetch and push all adversaries detected by Lumu in the last 30 days to a user-defined Trend Micro Web Security Custom URL Category.
Task: fetch Lumu detected adversaries filtering by type
To specify the types of adversaries you want to filter in your queries, use the option --adversary-types ADVERSARY-TYPE . If you need to set more types of adversaries, you can repeat the option as follows:
For this example, the script will fetch Lumu detected adversaries of types C2C and Mining .
Task: run with .config file
You can run the integration using a configuration file where you can save the required arguments in the form of <argument_name>=<value>, one argument per line. In the <sophos-lumu> path, save a file named .config with your configuration. Following, you have a sample of the format of the file.
- ## TMWS Lumu configuration file
# TMWS
username=<TMWS_USERNAME>
password=<TMWS_PASSWORD>
# If the category does not exist, the integration attempts to create it
custom_category=<TMWS_CATEGORY>
# Lumu
company-key=<DEFENDER_KEY>
# Misc
days=30
adversary-types=C2C
adversary-types=Malware
adversary-types=Mining
adversary-types=Spam
adversary-types=Phishing

Task: Clean records
When the script is run with the –clean flag, it will erase all Lumu records created.

Task: save log output to file
Use the argument --logging file to store a record of all tasks run. Using this, the entire script output will be redirected to a file named lumu.log in the script root path ( <twms_lumu_root> ).
Other tasks
The above samples can be combined according to your needs.
Further considerations
To run the script on a timely basis, consider implementing a Scheduled task in Windows or a Cron task in Unix-based systems. We recommend that the scheduled job runs every 30 minutes.
Following, you have an example of how this Cron job should look using the recommended time.
It’s recommended to add the --logging file argument to any scheduled task. It will record all the output in the log file for further reference. If you have created a configuration file, your crontab entry doesn’t need arguments. It should look as follows:
If you need to work with another scheduling time, you can use the crontab guru service.
To avoid race conditions, you can run only one instance. If you have one running, the second one will be canceled immediately.
Expected results
After running the script, all queried adversaries will be pushed into the selected Custom URL Category as follows:
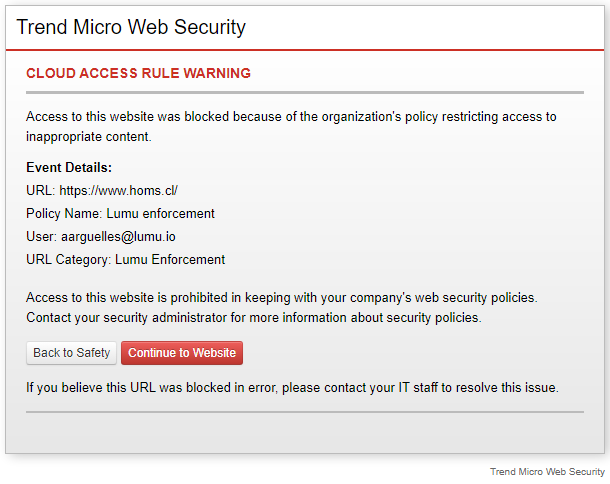
Troubleshooting and known issues
To identify failures in the script execution, use the -v flag. The script execution log will show more detailed information.
Another instance is running
If you receive the following error.
There could be another instance running. To check this, open the pid.pid file in the integration folder. This file stores the process id if it’s running. Search for this process in your system. The following pictures show the process in Windows and Linux.
If the previous validation indicates that another instance is running, please, check its progress using the integration’s log lumu.log .
Get an AI Summary
Related Articles
Trend Micro Apex Central Custom Response Integration
Before going through this article, check our Out-of-the-box App Integrations category. This is the recommended way to integrate the components of your cybersecurity stack with Lumu. If the product you are looking to integrate is there, it is advised ...Forcepoint Web Security Cloud Custom Response Integration
This article shows how to leverage the Lumu Defender API and Forcepoint Web Security Cloud to mitigate security risks. Forcepoint Web Security Cloud service doesn't have a REST API, so this script simulates the actions run by an admin user to feed a ...Trend Vision One Out-of-the-Box Response Integration
Requirements Trend Vision One: Make sure you read the Suspicious Object Management article on the Trend Vision One documentation thoroughly to ensure a smooth process. Lumu License An active Lumu Defender subscription Configure Trend Vision One Trend ...DNSFilter Custom Response Integration
This article shows how to leverage the Lumu Response API and DNSFilter API to mitigate security risks. Requirements An active DNSFilter subscription. A DNSFilter Pro subscription or up is required. Script host. A scripting host is required to deploy ...Bitdefender Custom Response Integration
Bitdefender Custom Response Integration This article shows how to leverage the Lumu Defender API and Bitdefender API to mitigate security risks. Requirements GravityZone Business Security Enterprise, cloud version, ...