Cisco Secure Endpoint Out-of-the-Box Response Integration
This article describes the required procedure to integrate Cisco Secure Endpoint with Lumu for automated response procedures. This is one of our featured Out-of-the-Box Response Integrations.
Requirements
- A Cisco Secure Endpoint Essentials or above subscription
- An active Lumu Defender subscription
Preliminary Setup - Cisco Secure Endpoint Portal
In order to set up the integration, you will need to prepare Cisco Secure Endpoint to interface with the Lumu integration. To do this, you will need to have the following information on hand:
- Base URL
- 3rd Party Client ID
- API Key
In the following steps, you will find how to obtain all four of these requirements.
Locating the Base URL
When you log in to the Cisco Secure Endpoint Portal, you will find that the URL can have one of these four formats:
- https://console.amp.cisco.com
- https://console.apjc.amp.cisco.com
- https://console.consumer.amp.cisco.com
- https://console.eu.amp.cisco.com
These formats describe the Cloud instance your Cisco service is associated with. With that info, you can identify which is your Cisco REST API base URL.
- https://api.amp.cisco.com
- https://api.apjc.amp.cisco.com
- https://api.consumer.amp.cisco.com
- https://api.eu.amp.cisco.com
From this previous list, keep on hand the Cisco REST API base URL that corresponds to your login, since it will be requested at a later stage of this guide.
Create API key
1. Log in on the Cisco Secure Endpoint Portal. Head to the panel on the left, and click on the Administration option found at the bottom. Then, on the pane that unfolds, click on the API Credentials option.2. Within the API Credentials panel, click on the New API Credential button on the right side of the screen.3. In the New API Credential window, fill out the Application Name with a descriptive name. Then, in the Scope field, choose Read & Write and click on the green Create button.4. After finishing the process of generating the API Credentials, a dialog box will appear displaying the 3rd Party API Client ID, and API Key. Store these values, since they will be needed for a later step of the setup process.Once you close this window, you won't be able to retrieve the API Key again. If you lose it, you will need to repeat all the steps from the beginning.
Create lists for Lumu integration
1. Head to the panel on the left, and click on Outbreak Control. Of the options listed, you only need to configure Custom Detections > Simple and Application Control > Blocked Applications. The following steps will detail the process following that order.2. Custom Detections - Simple functions similar to a blocklist: These are files you want to detect and quarantine.An entry in a Simple Custom Detection list will not only quarantine future occurrences of the file but, through Retrospective, will also quarantine instances of the file on any endpoints where the service has already encountered it.a. Choose a name that best suits the integration with Lumu, such as Lumu Detections - Simple List. Enter it in the Name field, click on the green Save button, and then on the Create button. It should then appear in the list belowb. Return to the Outbreak Control pane to proceed with Application Control > Blocked Applications.If your company has a specific naming convention, you can use that instead.3. Application control - Blocked applications are files you do not want to allow users to execute but do not want to quarantine.Use this for files you are not sure are malware, unauthorized applications, or to stop applications with vulnerabilities from executing until a patch has been released.a. Choose a name that best suits the integration with Lumu, such as Lumu Detections - Blocked List. Enter it in the Name field, click on the green Save button, and then on the Create button.If your company has a specific naming convention, you can use that instead.These lists are subject to caching as specified under the Cache tab in your Policies. The default length of time a file is cached depends on its disposition, as follows:
Integration Setup - Lumu Portal
This section of the article describes the steps that must be completed on the Lumu Portal to properly set up the Cisco Secure Endpoint Response Integration. To start, log into your Lumu account through the Lumu Portal.

Integrations are also available for Lumu MSP accounts. To access them, log into the Lumu MSP Portal.
1. In the Lumu Portal, head to the panel on the left and open the Integrations drop-down menu. Then,click on Apps. Click on the Response tab on the right to filter the available integrations accordingly.2. Locate the Cisco Secure Endpoint integration. The list is organized in alphabetical order from A to Z. Click on the Add button.3. On the window that opens, familiarize yourself with the integration details as well as best use cases and requirements. Next, click the orange Activate button to start the integration setup process.4. A popup will appear asking you to fill in Name and Threat Types. Make sure the name of the integration is meaningful and descriptive, and then choose the Threat Types you want the integration to push to Cisco Secure Endpoint. When done, click on the orange Next button.5. Choose the Base URL that matches your server. This can be found in the Locating the Base URL step of the Preliminary Setup - Cisco Secure Endpoint Portal section.Enter the Client ID and API Key, which were obtained in the Create API key section of the Preliminary Setup - Cisco Secure Endpoint Portal section, and click the Activate button. Lumu will verify the accuracy of the credentials provided.6. Choose the Simple Custom Detection List and Application Block List created in the Create lists for Lumu integration section. To finish, click on the orange Activate button.7. The integration is now created and active. Now, the Lumu Portal will display the details of the created integration: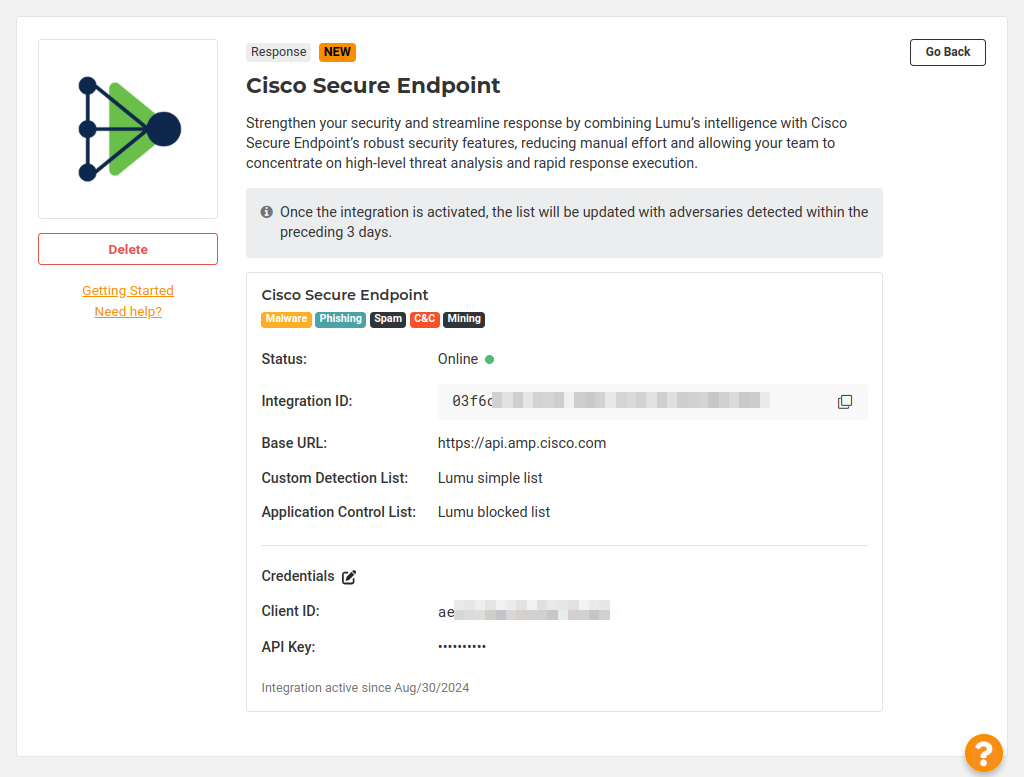
Final Steps - Validate the Integration on the Cisco Secure Endpoint Portal
After the integration is activated, you can verify it is working properly by heading to the panel on the left, and clicking on Outbreak Control. Both Custom Detections > Simple and Application Control > Blocked Applications lists will be updated with confirmed compromises detected by Lumu within the past 3 days.
Custom Detections > Simple
Application Control > Blocked Applications
Get an AI Summary
Related Articles
Lumu Out-of-the-box Integrations
For getting started with Lumu integrations with third-party solutions, consult our Integrations guide. Lumu's Out-of-the-box (OOTB) integrations are a seamless and convenient way to integrate Lumu with other solutions in your cyberdefense stack to ...Sophos Endpoint Protection Out-of-the-Box Response Integration
To learn more about Out-of-the-box Integrations and their benefits, please refer to this article. Requirements Sophos Central Sophos Central Account Access. API Token. You can obtain it in the API Token Management console. Lumu License An active Lumu ...Cylance Endpoint Security Out-of-the-Box Response Integration
This article describes the required procedure to integrate Cylance Endpoint Security with Lumu for automated response procedures. This is one of our featured Out-of-the-Box Response Integrations. Requirements Below you will find the technical ...Cisco Firepower Out-of-the-box Response Integration
To learn more about Out-of-the-box Integrations and their benefits, please refer to this article. The Lumu Defender API offers a framework to help you leverage Lumu’s integrations with your existing cybersecurity stack, including Security Information ...Harmony Endpoint Out-of-the-Box Response Integration
This article describes the required procedure to integrate Harmony Endpoint with Lumu for automated response procedures. This is one of our featured Out-of-the-Box Response Integrations. Requirements An active Harmony Endpoint Basic or above ...